“Trust but verify“
An old proverb but a wise one… You may have MFA enabled in your organization but are you confident on its efficacy?
not all mfa are made equal…
MFA Authentication Method Strength
Danger
At critical risk of account compromise.
Weak
Weak MFA method gives a false sense of security.
Medium
Yesterday’s strong MFA methods are no longer the best.
Strong
Reduces the chance of MFA bypass the most.
6 attack vectors you can protect with the right MFA setup
E-mail Phishing
Phishing emails are the #1 attack vector used by bad actors. Even if a user is tricked into entering their password on a fake website, the attacker still cannot log in easily without the second factor, if configured with secure method.
Credential Theft
If a user’s password is stolen from a breached database or lifted by malware (like a keylogger) from their device, MFA acts as the essential second barrier, preventing the thief from using the compromised password to access the account.
Account Takeover
This is the ultimate goal of many attacks. By preventing unauthorized access from phishing and credential theft, MFA directly stops attackers from gaining full control of a user’s account, preserving their access to email, financial data, and other sensitive information.
Adversary in the Middle (AiTM) Attacks
In a sophisticated AiTM attack, a hacker intercepts the communication between a user and a legitimate service to steal not just the password but also the session cookie after a successful login. Phishing-resistant MFA, specifically using FIDO2 standards, cryptographically binds the login to the legitimate website. This prevents the stolen session token from being successfully used on the attacker’s machine, neutralizing the attack.
SIM Swap Attack
Another sophisticated attack where an attacker tricks a mobile carrier into transferring a victim’s phone number to their own SIM card, they can intercept SMS-based MFA codes. However, if the user is protected by a secure MFA method, the SIM swap is rendered useless as these methods are not tied to the phone number.
Remote Access Compromise
Employees often use credentials to log into corporate VPN from remote locations. If an attacker acquires an employee’s password, they could gain access to the entire internal corporate network. Enforcing MFA on VPN logins ensures that even with a stolen password, the attacker cannot establish a remote connection, thereby protecting sensitive internal company resources from unauthorized access.
Modern MFA is no longer optional- it is a necessity.
Having the wrong MFA strategy can be like living in a glass house. Gain confidence of your organization’s MFA implementation with a MFA gap assessment from ROKIT Cyber.
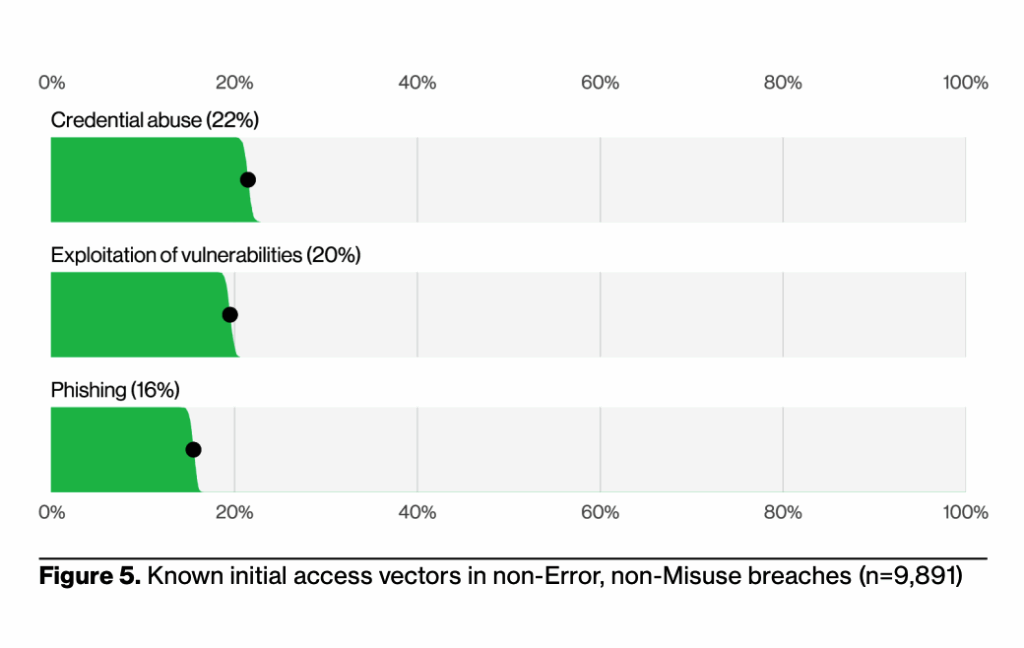
Credential theft
Compromised credentials remain the leading method for initial cyberattacks.
Attackers favor them because they can be reliably obtained through theft, guessing, data leaks, or malware. According to the 2025 DBIR, the misuse of credentials is the most prevalent tactic in phishing, ransomware, and web application attacks. Last year, 22% of all breaches started with credential abuse, while stolen credentials were used in 88% of basic web application attacks.
MFA bypass
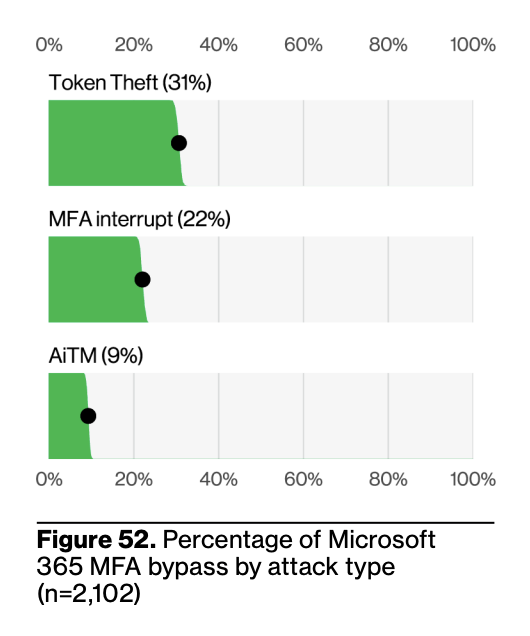
MFA bypass attacks prevalent
Attacks that circumvent multi-factor authentication (MFA) are becoming more common and advanced. Traditional MFA methods that can be phished, like one-time passcodes and push notifications, are proving vulnerable. Key attack vectors include:
- Token Theft: Hijacking session cookies or tokens to bypass authentication.
- MFA Interrupt: Bombarding a user with push notifications to coerce approval.
- Adversary-in-the-Middle (AiTM): Intercepting the MFA process in real-time.
These successful bypasses frequently lead to serious outcomes such as ransomware, account takeovers, and further network infiltration.

Is your business a glass house?
Our comprehensive MFA gap assessment can help you sleep better at night.
Why use our service?
- Ensure all your M365 users are on the MFA policy.
- Verify if the effective MFA policy is using legacy methods of MFA that is prone to bypass attacks.
- Any findings include steps to remediate.
- For added benefit, you can send our final report to your cyber insurance provider as proof of effective control.
What our engagement looks like
Our comprehensive suite of professional services caters to a diverse clientele, ranging from homeowners to commercial developers.
1. MFA Assessment
2. Report Delivery
- Review your M365 MFA configuration
- Audit MFA logs for efficacy
- Review against best practice controls
- Deliver assessment report
- Deliver recommended plan of action (if applicable)
3. Remediation
4. Final Delivery
- Remediation plan as deliverable if necessary for your internal staff’s reference
- If requested, we can complete remediation for additional cost
- If purchased, a final report that is ready for submission to cyber insurance provider will be provided
Gain confidence in your MFA setup
Contact us today for a quote!
“ROKIT Cyber has helped us save thousands of dollars and qualify for the best cyber insurance policy coverage”
Scott Barrett
CEO, Real estate development firm
